
Bulldog CTF Walkthrough
It has been a while since I did a CTF so i decided to dive into one and I selected the Bulldog CTF created by Nick Frichette, you can find it here https://www.vulnhub.com/entry/bulldog-1,211/. It was a great exercise that helped remind me of some basic things to check when doing pen tests or CTFs. I highly suggest doing them as they really help keep your skills sharp in a safe environment. You might learn a thing or two as well, I know I did.
The goal of this CTF is to access the root folder and grab the flag from there.

To start any CTF you need to get it running on your hypervisor, I used Virtual Box for this one and from my experience most CTFs work well with Virtual Box. Once you have it up and running the VM will give you its IP. I generally run it on the Host Only adapter so it stays off any network im connected to.
Once the box was up the first thing I did was run a full nmap port scan with OS and service detection. I also exported the data to an xml file in case I wanted to import it to metasploit or something later.
Nmap –A –p- -ox /tmp/Bulldog.xml 192.168.56.101

I found that SSH was running on port 23 and a web server was on port 80 and 8080.
I loaded up metasploit and started brute forcing SSH in the background using a password and username list from the SecLists github, https://github.com/danielmiessler/SecLists. This did not yield any results.
I fired up burp suite and proxied it through my browser then navigated to the pages on 80 and 8080, they both looked the same, with a home page and one link to a Public Notice listing a recent hack. I also started spidering but didn’t notice anything just yet.

I checked the source of each page and didn’t find anything worthwhile. I also checked the Robots.txt file and was given the below notice of the German Shepard Hack Team who previously owned the system.

On a whim I decided to append admin to the home page, low and behold there was an admin page exposed.

After checking the view source and spending some time hitting this with SQLi, Blind SQLi, Command Injection, Common Passwords and XSS with no luck I decided to move on. A quick check on exploitdb.com didn’t turn up anything worthwhile for Django either and there was no list of a default username or password for the installation.
I was stuck for a bit but then decided to do some more recon, I ran dirb against the site and discovered a dev url.

Navigating to this gave the following, http://192.168.56.101/dev/

So this looked very interesting, it had a bunch of information on the attack and a list of emails. The attackers had exploited dirty cow to own the server.
Also there was a link to a web shell, http://192.168.56.101/dev/shell/ which led to this.

Back on the dev page I viewed the source, JACKPOT!!

It contained hashes next to each user!

I ran Hash-identifier to check their hash type, it came up as SHA-1

Then I ran them through John the Ripper

Right away I got a hit for the Back-up Team Lead Nick, his password was bulldog! I let john keep running for now to see if anything else cracks.
I navigated to the admin page and logged in with the new credentials, I was into the admin interface, but there was nothing I could do?!

I then remembered the web shell page at http://192.168.56.101/dev/shell/, when I navigated to it I was now logged in! I had the access I needed albeit with limited commands.

Running pwd gave me the directory and I saw I was in the django user bulldog directory.

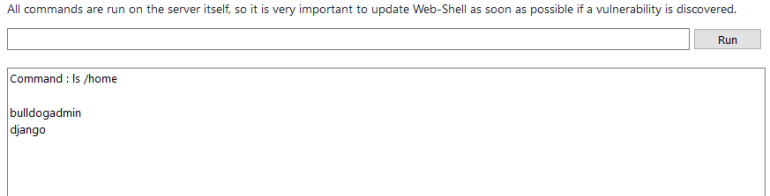
I also ran ls /home to see whatever other users had directories here.
And why don’t I see if I can cat the /etc/passwd file and /etc/shadow file while I’m at it.
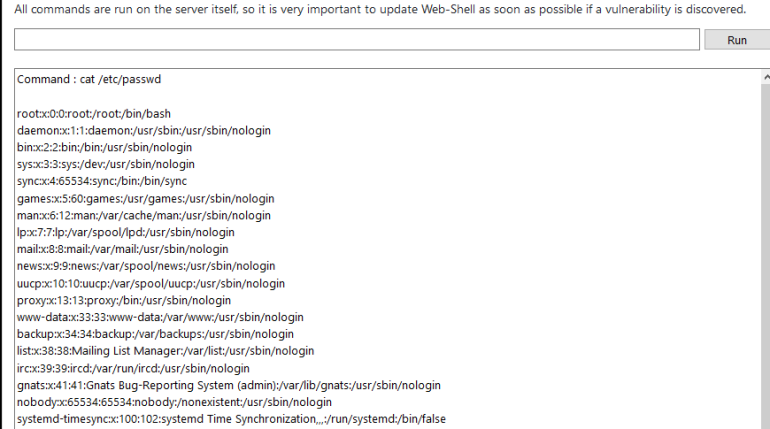
I got an error for the /etc/shadow file.

And I doubted it was this easy but I tried to look in the root folder too! I got the same error as above.
Then I ran ls -la to review what was in my main folder, this didn’t give anything I could use just yet.

I decided to check the bulldogadmin home directory, there was some interesting things here especially the hiddenadmindirectory.

Checking the directory gave me two files.

I promptly checked the notes file which talked about what was most likely the customPermissionApp.
Now here was the snag, I could only send limited commands but I tried the file command anyways, I encountered the below response when running it.
INVALID COMMAND. I CAUGHT YOU HACKER!
So I tried a couple of ways to bypass this and it turns out I could use && to send whatever command I wanted.

So this is an executable, for a while I thought maybe there is a way I can run this to raise my privileges but nothing worked. So I tried running strings against the file. And what was this?

Spelled out it was “SUPERultimatePASSWORDyouCANTget”! Time to check if this was really a password, so I tried the next easiest thing I could think of, I sshed to the box using django and this password, I had a shell!!!

I tried to cd to the /root folder but got a permission denied, so I tried sudo su and was able to elevate my privileges with the password I found. Then I changed to the root directory, and ran ls. Right there was the flag!

I ran cat on the file, did a dance

and then read the message.

I hope you enjoyed the write up!

You must be logged in to post a comment.